Why is Visibility into OT Environments Crucial?
The significance of Operational Technology (OT) for businesses is undeniable as the OT sector flourishes alongside the already thriving IT sector. OT includes industrial control systems, manufacturing equipment, and devices that oversee and manage industrial environments and critical infrastructures. In recent years, adversaries have recognized the lack of detection and protection in many industrial systems and are actively exploiting these vulnerabilities. In response, IT security leaders have become more aware of the need to protect their OT environments with security monitoring and response capabilities. This development was accelerated by severe past cyber incidents targeting critical OT environments and even causing physical damage to infrastructures. Given the pivotal role these systems play in business operations and modern society, ensuring their security is of utmost importance.
The underlying trend is clear: OT and IoT networks are progressively integrated with traditional IT networks for management and access purposes, leading to increased communication between these devices both internally and externally. This not only affects the networks itself but also carries significant ramifications for the security teams responsible for safeguarding the environment. Although this convergence of OT and IT offers numerous benefits, such as enhanced efficiency and reduced operational costs, it also gives rise to new security risks and challenges, rendering OT environments more vulnerable to cyber threats. As evidenced by past attacks, these threats often go undetected due to insufficient security monitoring, allowing threat actors to remain undetected for extended durations. As a result, achieving holistic visibility and effective anomaly detection in OT environments is pivotal for maintaining steadfast security and control.
What Challenges Arise in Monitoring OT Environments?
First and foremost, understanding the unique threat landscape of OT environments is crucial. Traditional IT security detection methods fall short in this context, as they require different sensitivity thresholds and more refined monitoring for network segments or device groups, as well as OT-specific detection mechanisms. Unlike IT attacks that focus on data theft, OT attacks typically aim for physical impact. Moreover, as recent examples demonstrate, ransomware in the context of OT is on the rise and directly affects the availability of control systems and safety.
Second, monitoring OT environments requires the consideration of various aspects, such as supplier access management, device management, and network communications. Controlling and overseeing supplier access to OT and IoT networks is challenging, as connections between external and internal networks can occur through various means like VPNs, direct mobile connections, and jump hosts. Another hurdle is device management, which encompasses update mechanisms and protection against unauthorized access or manipulation. Implementing regular updating routines and deploying Endpoint Detection & Response (EDR) on OT and IoT devices is often limited or infeasible. The variety of devices, their life spans, and device-specific operating systems make deploying security software to monitor OT devices difficult and cumbersome.
Third, traditional IT network detection methods require in-depth protocol knowledge, which, in the OT context, includes a wide range of different protocols and attack scenarios absent in traditional rule sets. OT network devices connect IoT sensors and machines using communication protocols uncommon in traditional IT networks. In terms of more intrusive security solutions, active vulnerability scanning methods can also be problematic in OT environments, as they may cause disruptions or even outages. The same applies to Intrusion Prevention Systems (IPS) because they could block network packets, impacting stability and business continuity in OT environments. As a result, passive network detection systems like Network Detection & Response (NDR) solutions are better suited for this purpose.
How Can I Effectively Monitor and Secure My OT Environment?
While secure access management and device lifecycle management are essential, their seamless implementation can be incredibly challenging. In this context, Network Detection and Response (NDR) solutions offer a non-intrusive and effective approach to monitoring OT environments. By focusing on communication patterns for OT devices, the intersection between IT and OT, and third-party access to OT networks, NDR systems provide comprehensive visibility and detection capabilities without disrupting industrial operations and business processes.
In particular, NDR solutions with advanced baselining capabilities excel at identifying new and unusual communication patterns that could indicate malicious activities within OT networks. Utilizing flow information for baselining, these NDR systems provide protocol and device-independent anomaly detection by learning who communicates with whom and at what frequency. Instead of manually configuring these parameters, the NDR learns the baseline and alerts the security teams on unusual requests or changes in the frequency. In addition, a flexible use case framework allows setting fine-tuned thresholds for OT-specific monitoring, including the ability to set load monitoring with network zone-specific granularity. Moreover, the use of Machine Learning algorithms allows for more accurate detection of anomalies and potential threats compared to traditional rule-based systems.
As a result, the passive monitoring capabilities of NDR solutions are vital for OT and IoT environments, where alternative monitoring methods may be difficult to implement or cause disruptions. ExeonTrace, a particularly robust and easy-to-implement ML-driven NDR system for OT environments, analyzes log data from traditional IT environments, OT networks, and jump host gateways, to provide a comprehensive and holistic view of network activity. Therein, the flexibility of integrating various third-party log sources, such as OT-specific logs, is crucial. Moreover, ExeonTrace’s ability to integrate with other OT-specific detection platforms enhances its capabilities and ensures extensive security coverage.
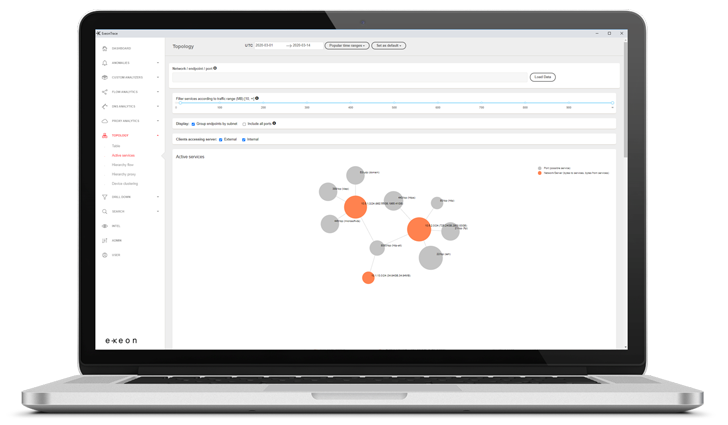 |
| ExeonTrace Platform: OT Network Visibility |
In summary, NDR solutions like ExeonTrace effectively address the distinct challenges of OT monitoring, establishing the Swiss NDR system as the favored detection approach for safeguarding OT environments. By implementing ML-driven NDR systems like ExeonTrace, organizations can reliably monitor and secure their industrial operations, ensuring business continuity through an automated, efficient, and hardware-free approach. Find out if ExeonTrace is the ideal solution for your business and request a demo today.

